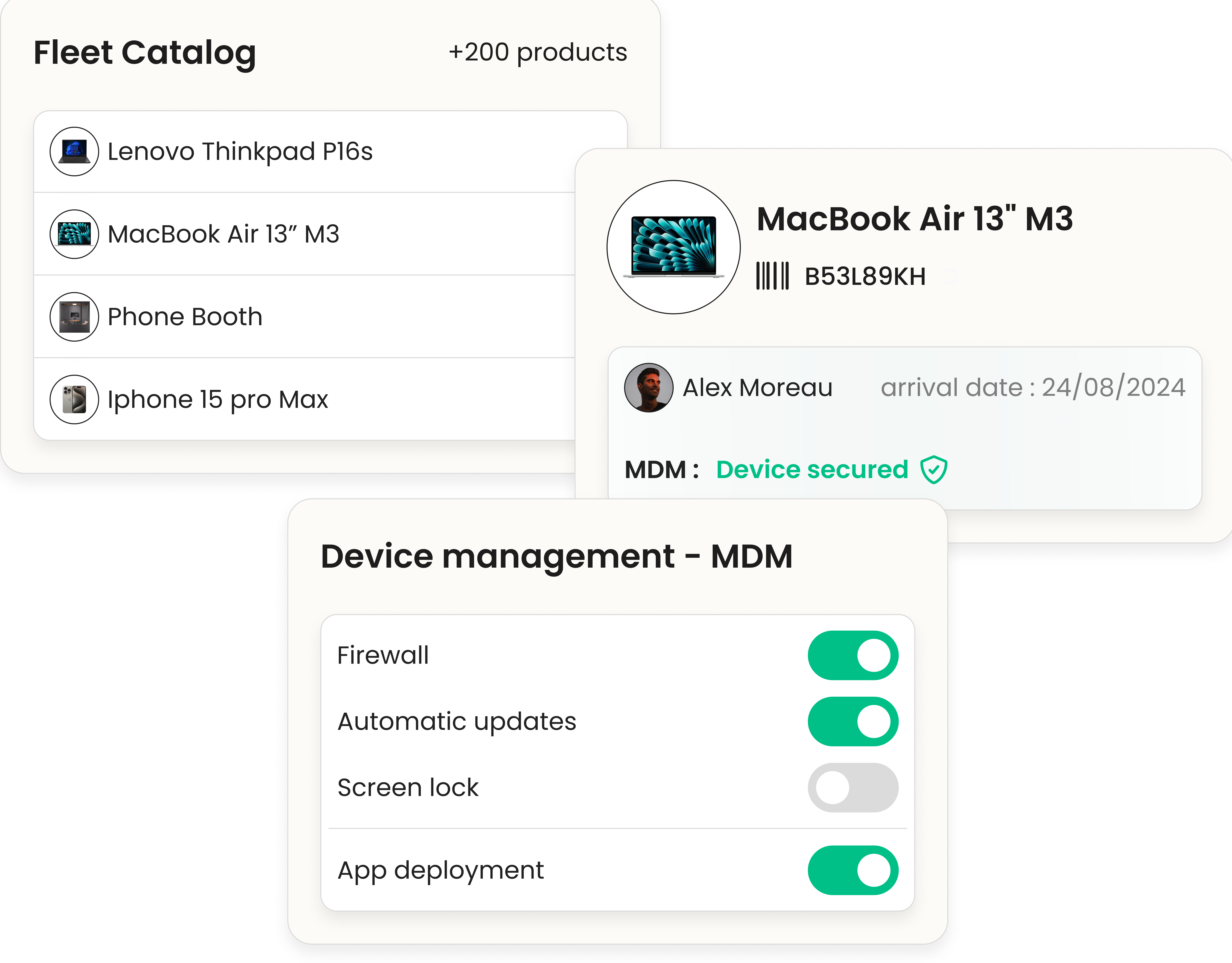
How it works
Why Fleet?
Catalogue
Resources
IT
Discover the sections
Mastering remote IT support: exploring Fleet's global support and AI copilot
Elevate your company's IT management with Fleet support. Discover our solutions designed to ensure the smooth running of your operations.
How to Manage the Theft or Loss of a Business Laptop: Essential Steps, Prevention & Protection
Learn how to effectively handle professional laptop theft with practical advice and preventive measures. Discover best practices and protect your data and equipment now
MDM - How to enroll Windows Devices with Zero Touch Deployment with Entra ID?
Learn how Fleet streamlines Windows device enrollment with Entra OOBE, manual setup, and automated management—ensuring secure, compliant devices with minimal IT effort.
MDM - How to enroll Windows Devices with Zero Touch Deployment - Microsoft Autopilot?
Learn how Fleet streamlines Windows device enrollment with Microsoft Autopilot Zero Touch and manual setup, ensuring secure, effortless device management from day one.
MDM - How to enroll Apple Devices with Zero Touch Deployment?
Learn how Fleet’s MDM simplifies Apple device enrollment with Zero Touch and manual setup, enabling secure, automated management and seamless device onboarding.
MDM - How to manually enroll your Apple devices?
Learn how Fleet’s MDM simplifies enrolling and managing Apple devices, with convenient manual enrollment, ensuring security and easy control.
Zero Touch Deployment and Manual Enrollment - MDM
Zero Touch Deployment automates device setup, while Manual Enrollment requires step-by-step configuration—learn which is right for your business.
ISO 27001 and SOC 2: Understanding Key Cybersecurity Standards
Discover the key differences between ISO 27001 and SOC 2 standards to enhance your organization's cybersecurity and select the standard best suited to your needs.
MacBook or Laptop: Which Suits Your Needs?
Are you unsure whether to choose a MacBook or a Windows laptop for your business? Discover the advantages and disadvantages of each platform in this comprehensive guide.
iPad Air or iPad Pro: Finding the right model for your team
Could the differences between the iPad Air and iPad Pro boost your team’s efficiency? Discover which tablet is better suited for your daily business needs.
The differences between prompt context, RAG, and fine-tuning
The differences between prompt context, RAG, and fine-tuning and why we chose prompting.
The survival guide to managing your IT in a hybrid environment
Fleet guides you through the challenges and opportunities of a flexible work environment: acquiring, managing, and renewing your IT assets.
Recommended items
The impact of AI on business IT equipment needs
Discover Fleet's survey conducted in 2025 on trends, opportunities and costs for AI integration in business.
IT Inventory Management: what you need to know
IT inventory management could be a nightmare, especially when your company is scaling or if you hire remote employees. HR or IT managers, learn the best practices to easy your day to day and save valuable time.
Remote Device Management Software: Key to Tackling Modern IT Challenges
Address the complexities of managing a remote workforce with Remote Device Management Software. Find out how to streamline operations, ensure security, and boost productivity with the right tools
Our most popular resources
Windows 10 end of support in 2025: Your complete guide to migrating to Windows 11
Windows 10 support ends October 14, 2025. Learn about the risks and get a step-by-step guide to transitioning to Windows 11.
How to Manage the Theft or Loss of a Business Laptop: Essential Steps, Prevention & Protection
Learn how to effectively handle professional laptop theft with practical advice and preventive measures. Discover best practices and protect your data and equipment now
MDM - How to enroll Windows Devices with Zero Touch Deployment with Entra ID?
Learn how Fleet streamlines Windows device enrollment with Entra OOBE, manual setup, and automated management—ensuring secure, compliant devices with minimal IT effort.
How it works
Why Fleet?